Assuming that you’re protected by default cloud security services can be a costly mistake. Supercharge your cloud security with proven strategies.
By 2025, 85% of organisations will embrace a cloud-first model. Security is a motivating factor, since it is widely assumed that data, applications, and workloads running on the cloud are inherently more secure than on-prem servers and protected by default cloud security services. This may be a costly assumption.

The most common risks of default cloud security
In Cisco’s latest Security Outcomes Report, nearly two-thirds of organisations report experiencing major security incidents that jeopardised business operations.
- Misconfiguration – essentially, a failure to put effective restrictions on a cloud-based service or system by leaving default settings, or failing to implement access controls and Least Privilege.
- Unencrypted data – unsecured data that can be easily viewed or accessed without the need for a decryption key, making it vulnerable to online breaches.
- Unsecure access points – failing to leverage authentication processes to ensure identity and authorisation prior to system, application or inbox entry.
- Lack of visibility – leaving data on remote servers out of sight, out of mind, and therefore failing to detect vulnerabilities before they become a real problem.
So, what measures are available to safeguard these vulnerabilities?

Encryption – scrambling data for improved security
Even if an attacker does manage to intercept or exfiltrate the data, it’s useless to them because they can’t decrypt it.
There are two types of commonly used encryption algorithms:
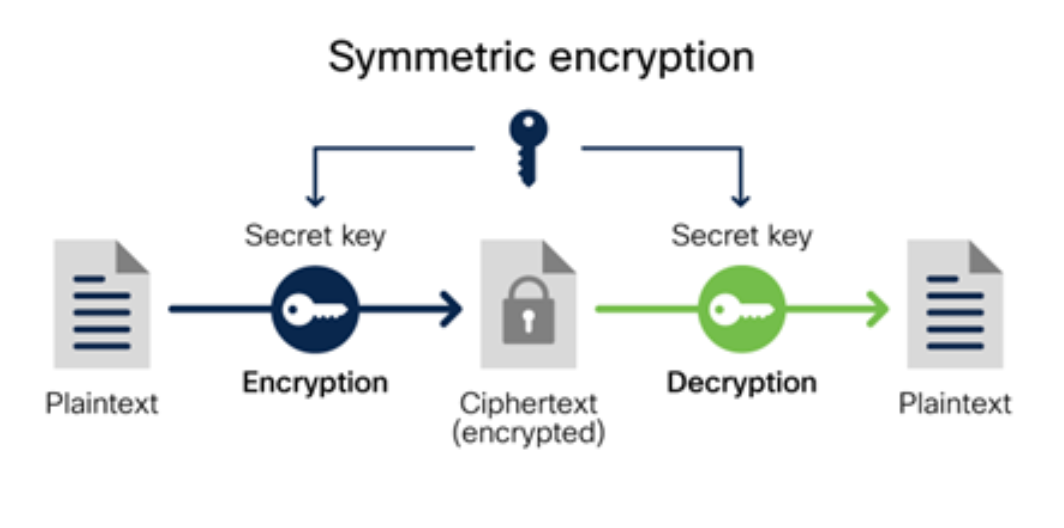
Symmetric encryption (also called shared key algorithm) which uses the same key for encryption and decryption. Because it uses the same key, symmetric encryption can be more cost effective.
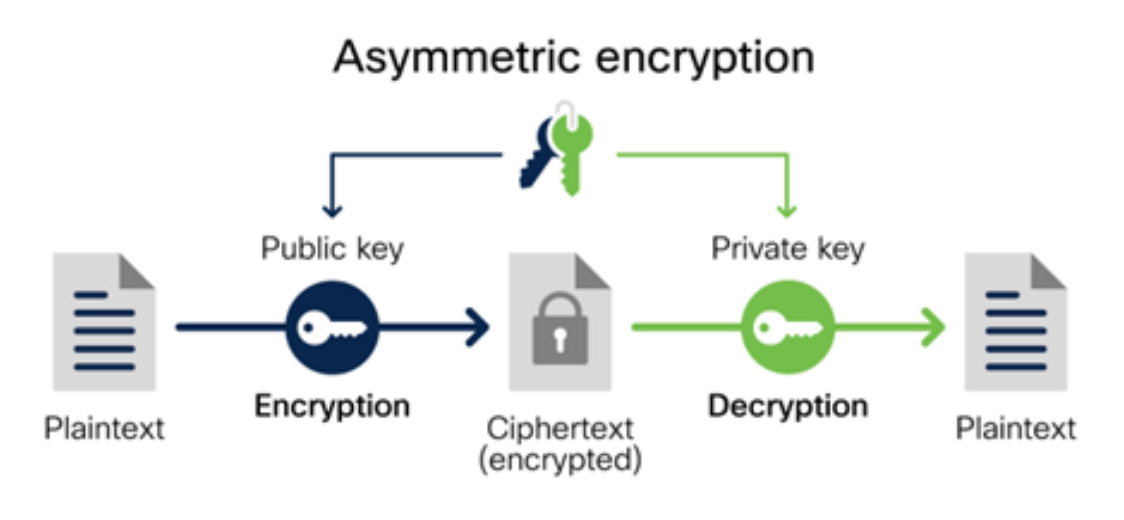
Asymmetric encryption (also called public key algorithm) which uses two separate keys: a public key and a private key. Often the public key is used to encrypt the data while a private key is required to decrypt the data. The private key is only given to users with authorised access – resulting in more effective, but costly encryption.
Outcomex and Cisco provide a range of security services that leverage encryption, including: Cisco Umbrella, Cisco Secure Endpoint and Cisco Secure Email Encryption.
Authentication – verifying identity for entry
Authentication is a vital security process used to protect systems and information in the cloud.
Patching – proactive protection of vulnerabilities
Patch management is the process of identifying, acquiring, installing, and verifying patches for products and systems that correct security and functionality problems and mitigate vulnerabilities. When it comes to patching, timing is crucial. When to install patches, which to prioritise and how to test them are common challenges.

Take it one step further – vulnerability assessments
Vulnerability assessments are a key part of ensuring a business has a strong security posture, used to identify, quantify, and analyse security vulnerabilities in the IT infrastructure and applications.
By focusing on IT infrastructure and applications, technology and sensitive data that are key to your business is kept secure and protected from cyber-attacks by deploying patches, improving security and functionality, and identifying weak configurations and unknown issues – complying with the major security regulatory standards. Interested in learning more? Take a look at our Vulnerability Assessment services:
Need help managing and monitoring your security portfolio? Through monitoring your networks, our team are able to detect and identify threats faster, discover any new malware variants, prevent/minimise downtime, improve preventative measures, security policies and compliance through enterprise-grade tools. In short, our fully certified security experts Need help managing and monitoring your security portfolio? Through monitoring your networks, our team are able to detect and identify threats faster, discover any new malware variants, prevent/minimise downtime, improve preventative measures, security policies and compliance through enterprise-grade tools. In short, our fully certified security experts monitor, prevent, detect, investigate, and respond to cyber threats on your business around the clock – so that you don’t have to. Learn more here.
Let us help you take care of the security management of your network. Our experienced security engineers are experts in offering end-to-end security services:
- Offering remediation guidance,
- Fixing lapses in security control measures
- Improving security policies.

Don’t make assumptions about cloud security, talk to Outcomex.



