In today’s rapidly evolving threat landscape, traditional security models no longer suffice. Perimeter-based defenses are ineffective against modern cyber threats. That’s why we embrace the Zero Trust security framework, because in cybersecurity, trust is a vulnerability.
Zero Trust is a security framework based on the principle: ‘Always verify, Never assume’. Instead, Zero Trust requires continuous verification and re-assessment of users, devices, and applications, ensuring only legitimate access is granted.
Here is how adopting a Zero Trust framework, can help your organisation build a a resilient, adaptive security posture that keeps up with evolving threats.
- Reduce attack surfaces and prevent unauthorised access
- Strengthen identity verification and device security
- Secure hybrid and multi-cloud environments with continuous monitoring
- Enhance compliance and regulatory alignment

In this 3-part video series, Wade Goudie, Pre-Sales Engineering Leader, Security Channels APJC at Cisco, joins Michael Van Zoggel, Managing Director at Outcomex, to discuss how Zero Trust can simplify all your security operations.
Enjoyed this series? Watch Building Security Resilience Series 1, here.
Outcomex delivers a comprehensive security strategy by integrating Zero Trust and advanced security solutions to safeguard organisations end-to-end:

Workforce
Ensuring only verified users and authenticated, secure devices can access applications through robust multi-factor authentication (MFA) and adaptive access policies that adjust to evolving roles, locations and devices.

Workloads
Securing cloud and on-premises applications by continuously monitoring and verifying access to critical business assets wherever they reside.

Workplaces
Protecting corporate environments, including data centers, offices, and IoT systems, with network segmentation and adaptive security policies that proactively mitigate threats
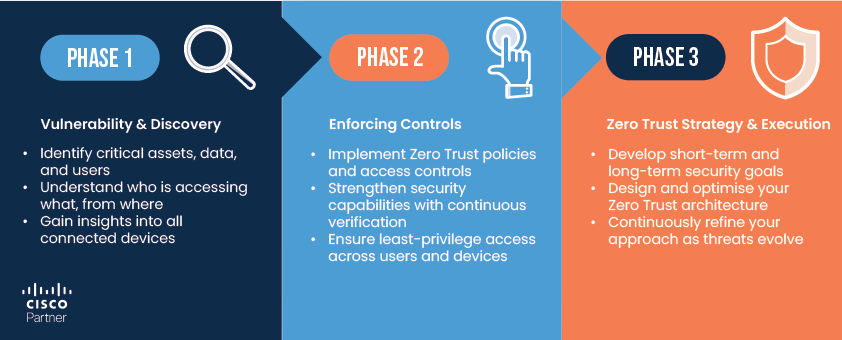
Zero Trust is a strategic journey that strengthens your security posture over time. Organisations are adopting a phased approach to implement Zero Trust effectively.
Here’s how you can break it down:
Featured Content
Learn how the Outcomexperts team with Cisco to deliver expertise and a modern Zero Trust mindset to help your business stay secure, productive, and ready for anything.

We can help you take the first step in your Zero Trust journey by providing a
free assessment to gain visibility across your assets.

